1Password Teams and 1Password Business are HIPAA compliant and can be used to securely store and share your electronic Protected Health Information. View and restore previous versions of items in your team Learn how to revert to a previous version of an item, restore a deleted item, and manage who can. The Expire Passwords feature allows you to expire passwords of all Okta-sourced users. Every Okta-sourced user will be forced to change their password they next time they sign in. Before you enable this functionality, consider the following: Active sessions remain active. The user is prompted for a new password the next time they sign in. This includes the Learning Portal, Help Center, okta.com and other Okta web properties.
With 1Password Business, you can automate many common administrative tasks using the 1Password SCIM bridge. It uses the System for Cross-domain Identity Management (SCIM) protocol to connect 1Password with Okta, so you can:
Provision
- Create Users. Users created in Okta will also be created in 1Password.
- Update User Attributes. Changing a user’s name in Okta will change their name in 1Password.
- Deactivate Users. Deactivating a user or disabling the user’s access to 1Password in Okta will suspend the user in 1Password.
Import

- Import Users. Users created in 1Password will be downloaded and turned in to new AppUser objects, for matching against existing Okta users.
Push Groups
- Push Groups. Groups created in Okta will also be created in 1Password, and group membership changes in Okta will also be made in 1Password.
Before you can configure Okta, you’ll need to set up and deploy the SCIM bridge.
To get started, sign in to your account on Okta.com , click Admin in the top right, and follow these steps.
Add the 1Password Business application to Okta
To add the 1Password Business application to Okta:
- Click Applications, then click Add Application.
- Find 1Password Business in the list and click Add. You’ll see the general settings for the integration, including the default application label “1Password Business”.
- Click Next, then click Done.
You’ll see the details of the application you just created.
Configure the integration
On the 1Password Business application details page, click Provisioning. Then follow these steps.
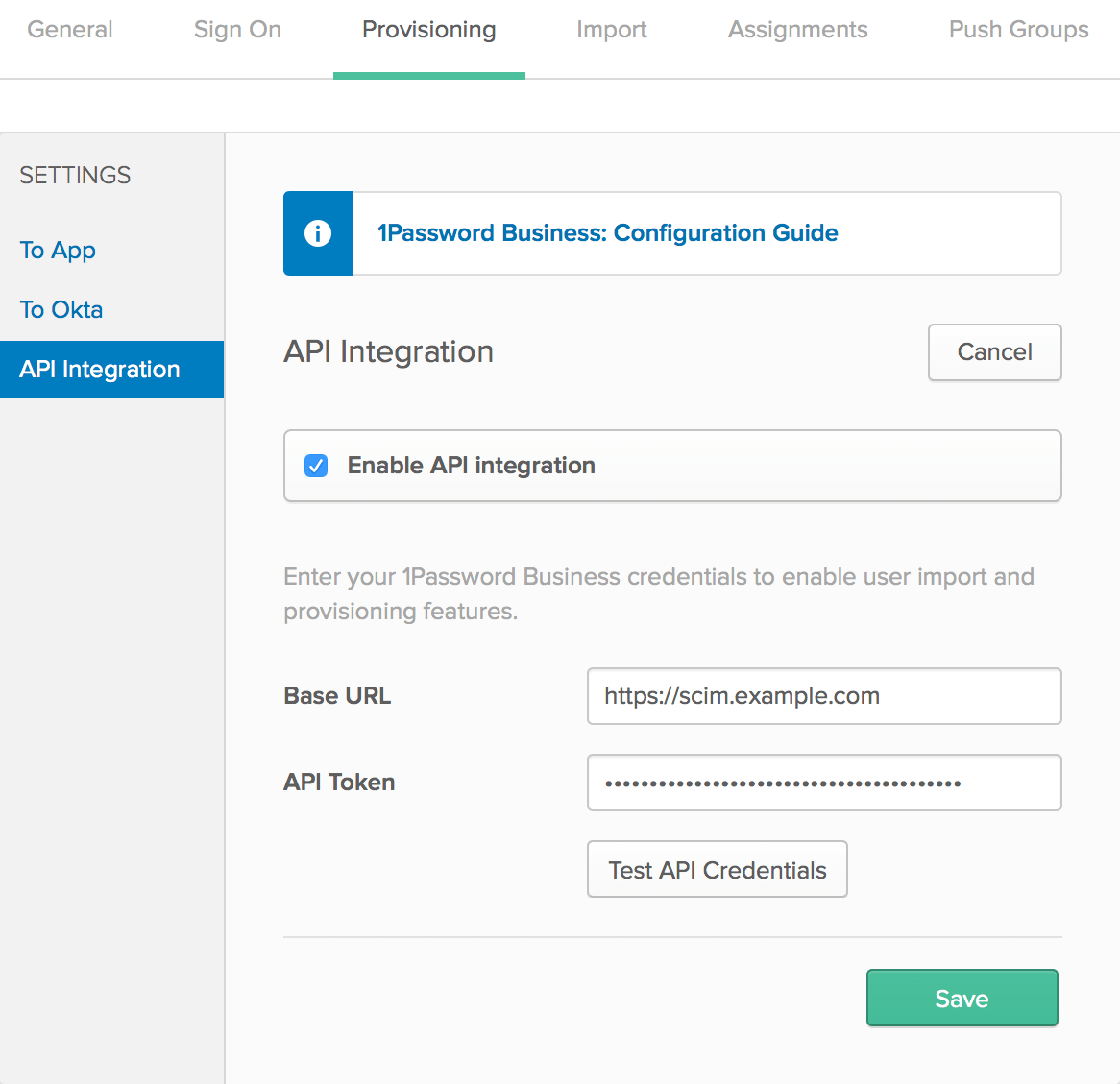
Set up API integration
Click Configure API Integration, then turn on Enable API Integration.
Enter your Base URL and API Token.
Base URL: the URL of the TLS-secured API gateway, proxy, or load balancer where you’ve configured the 1Password SCIM bridge. For example:
https://scim.example.comAPI Token: your OAuth bearer token
Click Save.
Get help if you don’t have your bearer token.
Set up provisioning to 1Password
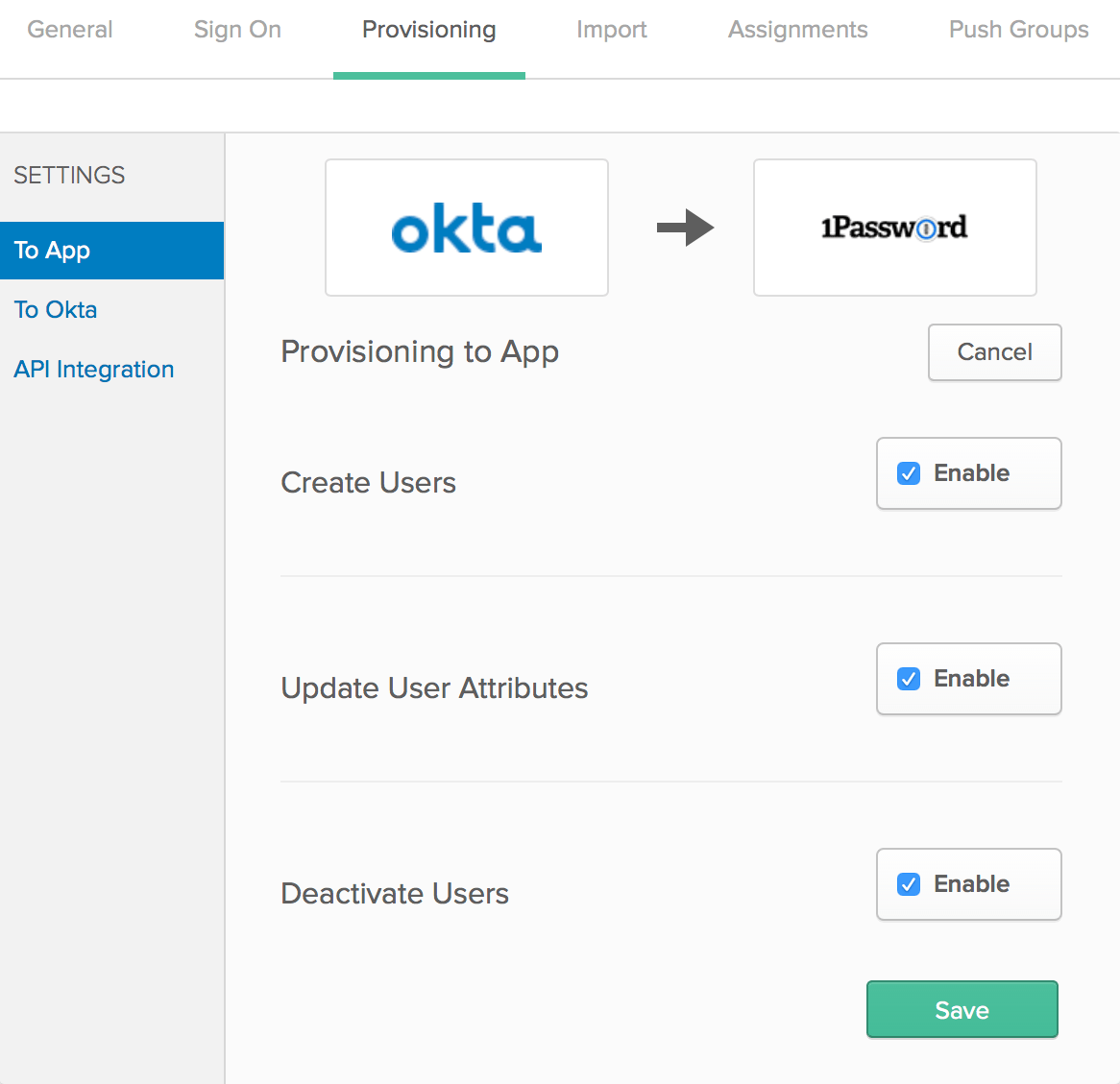
Click To App in the sidebar, then click Edit.
Turn on these options:
- Create Users
- Update User Attributes
- Deactivate Users
Click Save.
Settings
To manage assigned users and groups, click Assignments. Then click Assign and choose Assign to People or Assign to Groups.
To turn off synchronization, click Active and choose Deactivate.
To change the region to match your 1Password account, click General, then change Region Type.
Learn more on the Okta Help Center.
Okta 1password App
Next steps
If you have existing groups in 1Password that you want to sync with Okta, add them to the groups managed by provisioning. Click View Details in the setup assistant or click Integrations in the sidebar and choose Manage. Click Manage in the Managed Groups section, then select the groups to sync.
If you’ve previously used the SCIM bridge, make sure to select any groups that were already synced with Okta. This will prevent problems syncing with your identity provider, including duplicate groups.
1password With Okta
The Expire Passwords feature allows you to expire passwords of all Okta-sourced users. Every Okta-sourced user will be forced to change their password they next time they sign in. Before you enable this functionality, consider the following:
- Active sessions remain active. The user is prompted for a new password the next time they sign in.
- You can use the App Password Health Report on the Reports page to monitor how your users reset their passwords.
- API tokens are not expired. API tokens are valid for 30 days and renew automatically with each request to Okta. For more information on API token expiration and revocation, see API token management.
- Bulk password expiration only applies to Okta-managed users, unless the Active Directory Password Reset or LDAP Password Reset feature is enabled. When password reset functionality is enabled, the passwords of users managed with Active Directory or LDAP delegated authentication are also expired. Your Active Directory and LDAP agents will continue to work even if the service account managed by Okta has an expired password.
- If you are responding to a security vulnerability, ensure that your applications are already patched and no longer vulnerable before resetting the Okta password.
- When a user's Okta password is changed, all applications assigned to the user that support Provisioning and are Sync Password enabled are updated with the new password.
- In the Admin Console, go to Directory > People.
- Click More Actions > Expire Passwords.
- Click Expire Passwords in the confirmation dialog box.
